Follow the Money: Unmasking Collusion and UBOs with Temporal Graphs


Introduction
Sophisticated criminals and sanctioned individuals are masters of concealment. They hide their influence behind complex webs of shellcompanies, trusts, and nominee directors, making it nearly impossible fortraditional KYC and due diligence checks to identify the Ultimate Beneficial Owner (UBO). To break through this wall of obfuscation, you need to go beyond static ownership charts and reconstruct the entire, evolving history of control and interaction.
The Corporate Shell Game
Trying to identify a UBO from static records is like tryingto solve a puzzle with most of the pieces missing. Criminals exploit this bycreating convoluted legal structures and making rapid, suspiciously timed changes to directorships or shareholdings to break the chain of evidence. A compliance check on Monday might show a clean bill of health, but a change of ownership on Tuesday renders it useless. This "corporate shell game" makes it incredibly difficult to connect bad actors to their illicit assets and activities.
Reconstructing the Truth Over Time
Pometry’s temporal graph engine is purpose-built to cutthrough this complexity. We allow you to ingest and connect diverse datasets - from corporate registries and transaction logs to director information - into a single, unified network view.
- Expose Suspicious Timing: Pometry doesn’t just show you the ownership structure today; it allows you to rewind and play forward, revealing suspiciously timed changes in control that are strong indicators of collusion. These techniques are especially critical when investigating complex, fast-moving fraud, such as the scandals surrounding the distribution of COVID-19 Protective Equipment.
- Automatically Surface Hidden Pivots: Leveraging Pometry’s temporal graph algorithms, analysts and investigators can automatically surface “common pivot points” - individuals, addresses, or phone numbers that connect seemingly unrelated corporate networks.
- Analyse at Scale and Speed: This deep analysis, which can be performed across terabytes of data in seconds, makes it possible to unmask the true UBO with a level of speed and certainty that manual processes could never achieve.
Conclusion
Move beyond superficial KYC checks to a deep, temporal understanding of ownership and control. With Pometry, you can proactively identify the patterns of collusion, reconstruct evolving corporate structures with confidence, and expose the hidden UBOs that pose a threat to your organisation.

You might also like
Discover insights and tools for data analysis.

The hidden failures of transformation
Why delivery optimisation is making transformation worse
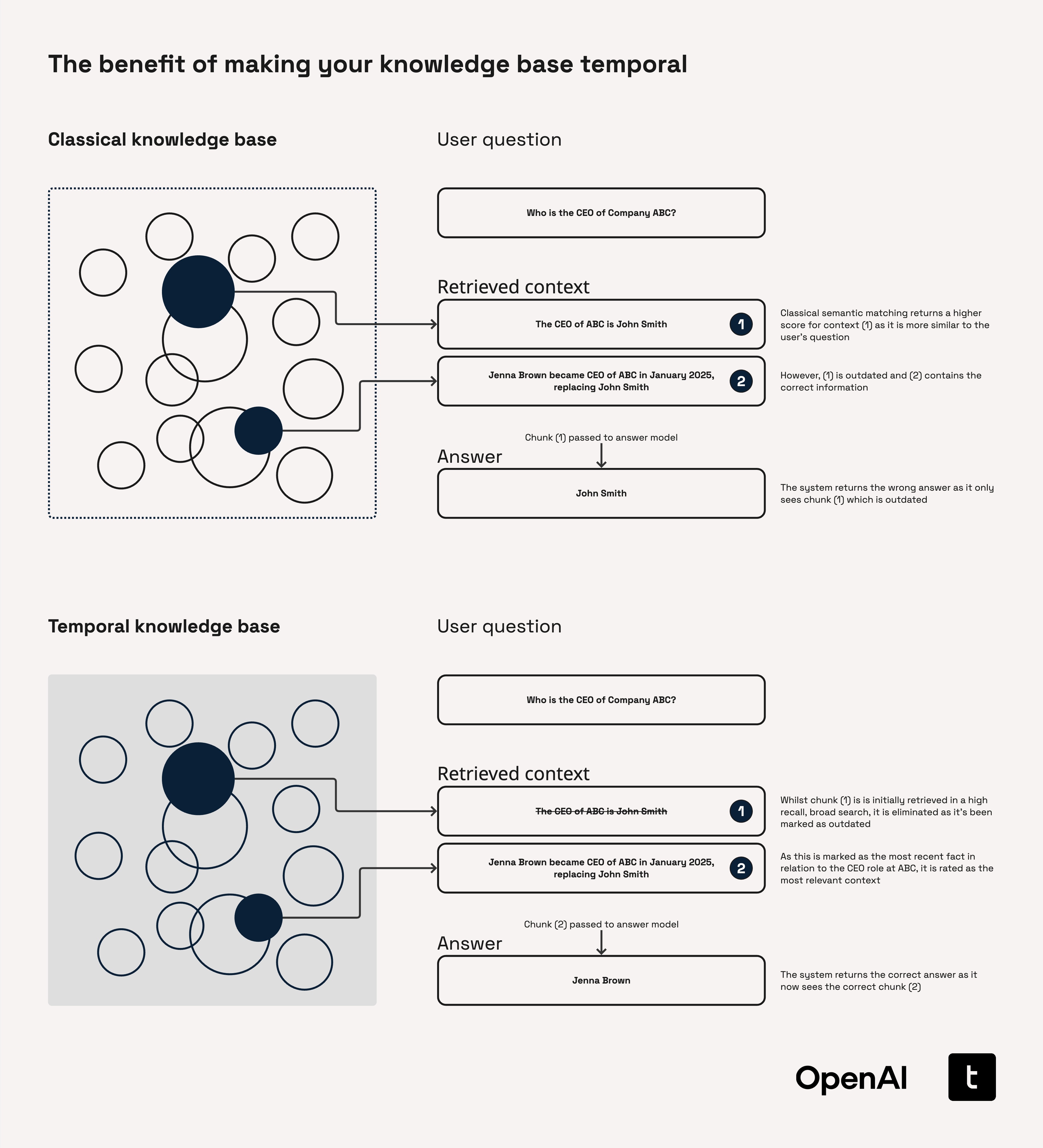
The Missing Link for AI Agents: Why a Native Temporal Graph is Non-Negotiable
Unlock Your
Data's Potential
Discover how our tool transforms your data analysis with a personalized demo or consultation.